Three Stories about Growing Up
- At January 24, 2013
- By Josh More
- In Business Security, Psychology
 0
0
There have been two stories in the media lately and one event on a private mailing list that have me thinking. First, the stories.
1) Former NFL Quarterback, Jon Kitna, has become a high school teacher. He did this as a way to give back to the community. However, the most important part of the story is how he is giving ba ck. This is a story about someone trying to change his community by teaching children that their actions have consequences, even if those consequences result in the entire team losing.
ck. This is a story about someone trying to change his community by teaching children that their actions have consequences, even if those consequences result in the entire team losing.
2) A Canadian computer science student by the name of Ahmed Al-Khabaz was expelled from Dawson College for running hacking tools against a system that contained data for numerous students. He found a flaw, reported the flaw, but because he did not have permission to run the test, he was kicked out. He has since been offered opportunities with firms and other schools.
3) On my private mailing list, a friend expressed concern over an issue in which one of his students sent a PDF of a book to the entire computer security class. This book was a copyrighted work by someone else that we both know. This was clearly illegal and, by most standards in the security community, unethical.
So, what do all of these stories have in common? Fundamentally, they’re about young people making mistakes. What might be hard to see, though, is that they’re also about adults making mistakes. We tend, in the Security and Legal communities to see the world in black and white. Dawson College expelled Ahmed Al-Khabaz because, in their view, he was “no longer suited to the profession.” There was discussion about expulsion in the private story as well, because of similar concerns. In other words, we have colleges taking a hard line on students that screw up and are kicking them out.
The problem, though, is that one of the best ways to learn is by making mistakes. Many of the best people we have in IT Security have checkered pasts. Many of the worst people we have in IT Security also have checkered pasts. While my own past is cleaner than most, I did cross the line a few times in school and got a talking to. I quickly learned both what to do and what not to do, but more importantly, how to do.
Actions must have consequences. Without pain, we do not learn. However, if those consequences are too severe, we don’t learn either. We give up.
If we look at these issues as a society, we have people working defense who are trying things and, if they try the wrong thing with the wrong person, they’re kicked out. We also have people working as attackers. These are well-paid individuals (due to the high risks involved) and are often highly skilled because they are not hampered by people trying to get them expelled or fired for experimentation. In fact, the more we take a hard line approach to these sorts of issues, the more likely we are to identify our best learners (the young people who make mistakes) and drive them to unethical and illegal activities, as we close the door to legitimate work in their face.
In a world where the attackers are massively out-competing the defenders, I have to ask whether this is wise.
Instead, consider Jon Kitna’s story. He’s adopted hard line rules for his football players. If they screw up, they’re out … but not completely … just a game or part of a game. They’re not off the team, they’re not kicked out of the community. This still means a mistake is punished, but done so in a way where people learn from it. Those who made the mistake get the most punishment. Those who supported the mistake while it was being made get a lesser punishment, and all of them serve as examples to keep everyone else where they need to be.
As people, we learn and grow over time. Of these three stories, which supports growth? Of these three stories, which people would you rather work with as adults? Who would you hire?
I know, for me, I’d take the under-educated, low-income kids over the college students any time. Why? It’s about community. Lincoln High School is making better adults than Dawson College is. The graduates from Jon Kitna’s football team might not be the best educated kids. They might need a lot of hand holding and training to make it in the real world, but they’ll have character. If I’m working a security problem with someone, I need someone I can trust. That means I need someone who has been raised to be trustworthy. Improvement is iterative and if you’re not given the ability to learn and grow from your mistakes, you’re just going to wind up making the same errors over and over again. As a security person, a professional and, really, just as an adult, I need people who have made mistakes, owned up to them and, where possible, fixed them. I need learners and I need people who can see the shades of grey in the world. I suspect that you do too.
(This post was originally published on RJS Smart Security)
Internet Theft and the Holidays
- At January 04, 2013
- By Josh More
- In Business Security, Psychology
 0
0
This is an older post. It originated over at RJS Smart Security and it just took me a while to get it posted here. Sorry for the delay.
As many of you know, when I am not protecting people and their businesses, I’m often out taking pictures. My camera of choice has been the Nikon d300, which is over five years old now. As with all technology, when cameras age, they become increasingly unreliable and it became apparent over a year ago that my camera was experiencing legacy issues. The weather protection was weakening, the sensor was staring to fail and the batteries were draining faster and faster. If I am going to practice what I preach, it was time to ruthlessly eradicate legacy.
“Ruthlessly eradicate legacy” is one of my mantras when it comes to infrastructure management. Older systems take a surprising amount of resources to maintain and use. Modern technology is easier to update, cheaper to operate and easier for people to use. It also has modern features that can drastically improve capabilities. With servers, this means killing all that no longer get updates (Windows 2000, for example). With cameras, it means time to say goodbye to my old friend and look at other options.
This is not a camera post, however, so I’ll cut short the decision process and say that I settled on a d800 or d800E. For my purposes, there are no differences, so I went out looking for a good deal. After all, Black Friday is coming and now is the time to look for electronics. This, however, is where the story gets interesting.
In doing my research, there were indications that while camera accessories go on sale periodically, the high-end camera bodies and lenses I like only drop in price when a successor comes out. This means I’m stuck at the high end unless I buy used. Moreover, in the Nikon world, warranty is a huge factor and is significantly reduced when you buy used, so it only makes sense to look at that option if you are going to save over 20% off the purchase price.
Which is why, when I found a d800E on Amazon, I got a little excited. In fact, I got a little too excited. I almost got scammed.
The list price on a new d800E is $3,299.99 (which is why my d300 got to be five years old before I considered a replacement), but this camera listed on Amazon.com was just $1,836.73. 56% off is clearly a better deal than 20% … but the deal is a little too good. In fact, it’s so good that a lot of people are going to leap on the deal, so I had to move fast.
Or did I?
See, the deal was too good. I got suspicious. Luckily, the seller had a note in their little logo icon that said to email with questions, so I did… not before I did a bit of research, though.
The company was Bissinger’s Inc., so I checked them out. They’re a St. Louis-based chocolate company. (Warning, if you click that link, your friends and family will be getting chocolate for Christmas, and your checking account is going to be a fair bit lighter.) At this point, I’m wondering why is a chocolate company selling a high-end camera? But since I want it to be real, I’m concocting ridiculous scenarios to make it seem legitimate. For example … “Maybe they bought the camera to take photos of their chocolates for the holiday season, but it was too complex for them?”
Anyway, there’s no harm in emailing them to find out, so this is what I send:
From: Josh
To: Bissingers
I am in the market for a D800E and see that you are selling one.
I have to ask before purchasing though, why a chocolatier would be selling a camera.
Is there something wrong with it?
I then cross my fingers, and go to bed with visions of massive megapixels dancing in my head. The next morning, I get this:
From: Bissingers
To: Josh
Hello,
the Nikon D800E 36.3 MP CMOS FX-Format Digital SLR Camera (Body Only) is in new condition ( it just had to be listed as ‘Used – Like New’ as the box has been opened), comes with all manufacturer supplied accessories, US model,1 year full warranty. It has not been used. The price is $1,836.73 including delivery.If you are wondering why the price is lower than the usual,it is because we have some promotional prices before holidays.Return policy is full money back in 30 days. If you want to buy send me your full name and delivery address to have your order placed with Amazon.
Many thanks
Heck of a deal, right? Except that, by this time, the camera has vanished off of Amazon. Still not wanting this to be a scam, I think that maybe they pulled it because they’re going to sell it to me. I send them the following:
From: Josh
To: Bissingers
I do want to buy. Is it still available? I see that it’s no longer listed on Amazon.
Here is the information you requested:
[My address here]
After all, if it’s a scam, all they have is my email address and name (which they had before) and my street address, which as a home owner is a matter of public record. When it comes to payment, it’ll go through Amazon, which links to my credit card. If it’s fraud, all I have to do is call my card company and dispute the charges. Right?
They reply with:
From: Bissingers
To: Josh
Ok,
Your order will be processed by Amazon
Thank you and let me know when you will receive the confirmation from them.
And I respond:
From: Josh
To: Bissingers
Do you need my amazon ID?
I’m curious as to how the payment will get to you.
I’m also curious as to when it will arrive.
Well, several hours go by and I hear nothing. I’m growing concerned. After all, I’m in Minnesota and they’re in St. Louis. They normally sell chocolate for around $50 a box. You’d think an $1,800 sale would be a big deal to them, right? I email them again:
From: Josh
To: Bissingers
I haven’t heard anything from Amazon yet?
Is there something that I need to do?
No response… and enough concerns have piled up I am suspecting a scam. They never directly addressed my concerns about a chocolate company selling the camera. They implied that they sell other electronics, but they are clearly a chocolate company. And they’re using Amazon in a way I’ve never seen it being used. I suspect it may be a grey market or possibly even a stolen camera. I’m wondering how anti-fraud protections work if you buy a stolen item, and I decide to just call them and get to the bottom of things.
Stepping outside of the Amazon.com system, I find their website and their contact page. I call the corporate office and tell them my story and find out their Amazon account had been hacked and it was a scam. This was deeply disappointing as I had, by that time, hoped I’d be able to get my camera and order chocolates for my family. Alas, such was not to be.
However, it did puzzle me how the scam worked. After all, I hadn’t given them any useful data. How would they get my money? Were they just incompetent criminals? This was well outside the realm of photography and I now had a professional interest. Time, of course, was the determining factor.
Later that night, the following email arrived:
From: Bissingers
To: Josh
Hi again,
I was informed by Amazon that they send you all the payment and delivery informations. Search your inbox carefully and also check your bulk/spam/junk folder because it might have arrived there. Please let me know asap.
Thank you!
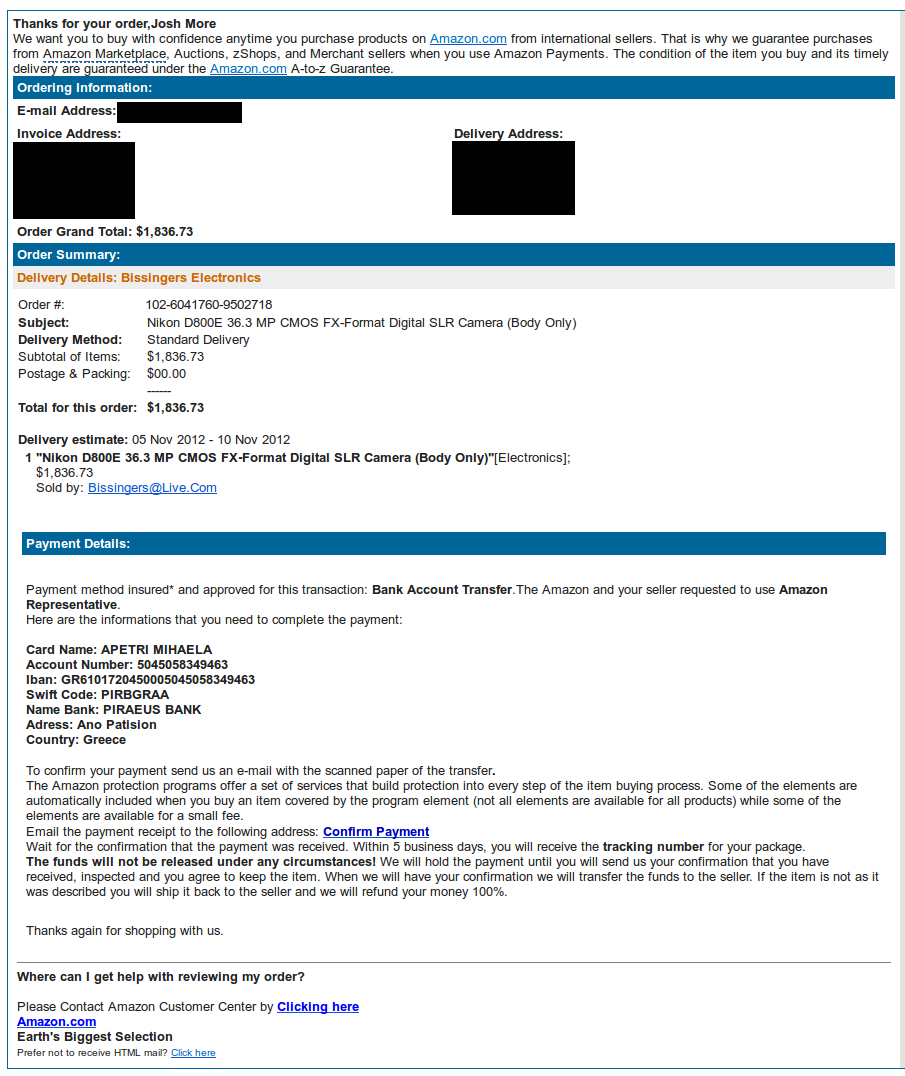
Ah hah. The payment was not, in fact, to come through Amazon, but would have an alternative system. For an attacker, this makes sense. After all, if they tried to accept payment from Amazon, Amazon can take it back when they are informed of fraud. I dutifully checked my spam folder and there were my instructions.
As you can see, it looks like a regular Amazon email, except that the payment section is a bit different. There are several interesting things to note here.
First, they prefer payment via bank transfer. This is common, particularly with overseas attacks, as once money leaves the American banking system, it can be notoriously difficult to get back. This should be a critical warning for most people, as it’s very different from the usual method of purchasing through Amazon. However, there is a grey market for electronic gear, and a lot of items come from overseas where warranties are different. So, it’s possible that a small percentage of people interested in high-end cameras would continue with the transaction.
Second, while most of the links are legitimate and match that of the Amazon.com template, three are different. The “Confirm Payment” link goes to [email protected]. The “Clicking here” and “Click here” links at the bottom go to [email protected]. They sound good, but a legitimate Amazon email would have all Amazon links. After all, if you bypass the Amazon system to sell your wares, Amazon makes no money. They work very hard to control the transaction.
Third, there was a bit of header analysis. If you like header wonkery, check the bottom of this post, but the three big things to notice are (1) the email came from private address space (10.x.x.x) and was sent through Google and (2) , the source address was “[email protected]”, but appeared to be from “[email protected]”. This is interesting because the email passed the SPF check and had all the expected anti-spam features. If I had not been hosting my email with Google, this likely would have been enough to bypass my filters. Finally, (3) all emails actually used for communication come from free email hosts. In this case, Microsoft and Google. If anyone can create an account there, I could be talking to anybody.
So, at this point, I decided to just wait and see what their next move was. I didn’t have to wait long:
From: Bissingers
To: Josh
Hello
It seems that one of my employees punt in the same package with yours 2 phones instead of 1.
Now you can’t receive the package until you will not send Amazon the same amount.
After you will do that,you will receive the package,but you have to send back the ohone and you will receive the money back for the second one.
Plus i will send you 50 USD as appologies for this inconvenience.
Contact us urgently.
Then, in less than a day:
From: Bissingers
To: Josh
Hello
I have already dispatched the package,but the package is on hold until you will make and send the payment informations to Amazon.
After that i will provide you also the tracking number.
Can you please tell me when are you able to make the payment?
waiting for your email asap.
This is where the attack starts matching the normal scam indicators.
They have so many victims that they can’t track them very well, and confuse my camera purchase with a phone purchase. There are the misspellings that we’ve come to expect from things like this. And finally, we get the social attacks.
Most scams use a hook to cause a reaction. The idea being that if you are reacting, they get to control you. If you take the time to stop and think things through, you take control back and can usually spot the scam. Common hooks involve Urgency, Uncertainty, Sex, Fear or Anger. In this case, it’s all about Urgency, Uncertainty and Fear. By setting the price so low, they drive urgency high, as you’re afraid that you might miss the deal. They then compound this by telling me there was an error in the shipment, trying to make me believe they are incompetent and if I act quickly, I can take advantage of their error.
The second email hypes the urgency, trying to get me to pay quickly. I did not reply, but if I had, the next step in a scam like this is to sweeten the deal if I were to act immediately, often by pretending to ship my non-existent camera with a bonus item (like a cell phone) overnight if I give them payment information immediately.
Of course, if I ever did give them my payment information, they’d empty my checking account and, if they’re with a larger attacker group, start using my account to traffic stolen funds.
This is a very long blog post, and I thank you for making it this far. Why did I go into so much detail? Because this Friday is Black Friday and quickly followed by Cyber Monday. Yes, this is the time we get great deals on electronic items, but it is also the time there is a massive uptick in scams. Basically, we’ve primed ourselves to be at risk for “too good to be true” offers, as some legitimate offers seem too good to be true, but are actually real. So, we can no longer rely on the old adage of “if it seems too good to be true, it probably is.” Instead, ask yourself the following questions as you review your deals:
- Is the price low enough you should be suspicious? Are you dealing with someone using only public email accounts? If either is true:
- Do you feel like you have to act immediately? (Urgency)
- Are the terms of the deal unclear in any way? (Uncertainty)
- Are you afraid that if you don’t take the deal, something bad will happen? (Fear)
- Are you paying in a way that you can easily dispute the charges?
If there is any concern, get someone on the phone. It’s a lot harder to come up with lies on the fly and you can often trip them up. If the deal starts to seem like a bad one, just stop. Don’t let them apologize or guilt you into anything. It’s worth paying a little bit more to know it’s not a scam.
————————————–
If you are interested in a deeper technical dive, here are the headers for the payment email. Enjoy.
Delivered-To: REDACTED_EMAIL
Received: by 10.112.148.37 with SMTP id tp5csp212198lbb; Mon, 5 Nov 2012 14:28:26 -0800 (PST)
Received: by 10.50.12.138 with SMTP id y10mr10891413igb.58.1352154505313; Mon, 05 Nov 2012 14:28:25 -0800 (PST)
Return-Path: Received: from mail-ie0-f174.google.com (mail-ie0-f174.google.com [209.85.223.174])
by mx.google.com with ESMTPS id s10si19571463ice.88.2012.11.05.14.28.24
(version=TLSv1/SSLv3 cipher=OTHER);
Mon, 05 Nov 2012 14:28:25 -0800 (PST)
Received-SPF: pass (google.com: domain of [email protected] designates 209.85.223.174 as permitted sender) client-ip=209.85.223.174;
Authentication-Results: mx.google.com; spf=pass (google.com: domain of [email protected] designates 209.85.223.174 as permitted sender) [email protected]; dkim=pass [email protected]
Received: by mail-ie0-f174.google.com with SMTP id k13so10488482iea.33 for ; Mon, 05 Nov 2012 14:28:24 -0800 (PST)
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=gmail.com; s=20120113;
h=mime-version:reply-to:sender:date:x-google-sender-auth:message-id
:subject:from:to:content-type;
bh=fEPMh0cdMOCy5Y1jBJj89FeNhCT6gsIQNKLFVfwBwyg=;
b=yItLaxIqhbh/AtFV1N/SvEacdDMoUtu/4Br8HGVW+dnPWzdnAx7DQK4ylTUvG9Rinc
ld827lC/tOxhXqRyJS2h+gyGmMn2KdtN4oHXhiRmVHJanpsVX/yRwzgvX8rZdAwXfEEZ
VRZN7Lw6xzjMF9TkRdWfi1LYDG5dXIfCtX8A1TuPwD6oM2ujK8k+OMxafCxlBLJEteQW
GqLVj0w733ig6pEO4C8QsjVzWJhKhVv+zMHzhTYPP58qdLtgbnZo2ddbSx/rwroIoRV/
6ETHAgL8liNzDI02lbM6Vx5RfJqDMR2rttQKq2Vqj4MFdc5UJI7mWWfwr54l1ZiOIjwR
z5pQ==
MIME-Version: 1.0
Received: by 10.42.163.5 with SMTP id a5mr3969473icy.37.1352154504571; Mon, 05 Nov 2012 14:28:24 -0800 (PST)
Reply-To: [email protected]
Sender: [email protected]
Received: by 10.64.82.201 with HTTP; Mon, 5 Nov 2012 14:28:24 -0800 (PST)
Date: Mon, 5 Nov 2012 17:28:24 -0500
X-Google-Sender-Auth: ZZYTCDwnOP6-ORmSRVSdM-vs2d0
Message-ID:
Subject: Your Order with Amazon.com
From: Amazon Services
To: REDACTED_EMAIL
Content-Type: multipart/alternative; boundary=90e6ba6e843ced2bd504cdc70061
Sophos: Pushing the Boundaries
- At December 26, 2012
- By Josh More
- In Business Security
 1
1
Several people have been asking me lately if I still prefer Sophos technology. After all, they recently released a bad update and Tavis Ormandy’s recent paper illustrated some design flaws in the product.
There’s spin on both sides. Unsurprisingly, Sophos is downplaying the issue and Tavis Ormandy’s tone in his second paper is much like that of his first. So I thought it would be good to explore the issues more fully.
I am disappointed in Sophos’s recent fumbles, but not disheartened. I still think that, for a great many companies, they have the best solution available.
There are two core problems here. The first is that of scaling. As companies grow bigger, they often become slower to react. Sometimes, they fail to adjust to their new reality. Sometimes, however, they get through it and become incredible companies. There are indications that Sophos is beginning the turnaround.
The second problem is industry-wide and has to do with market-splintering. Today, we are facing a splintering security vendor space and reports like the ones from Tavis are a symptom. Reports we’ve been getting for the past few years about AV and IDS being “dead” is yet another symptom. There’s nothing wrong with these reports and it’s good that people are thinking about the issues. But unfortunately, they’re missing the big picture.
In a splintering space, there is an increasing deviation between what a product actually does and how it is branded. This continues until the vendors wake up and pivot their branding to better match what they actually do. This always takes longer than we’d like, because employees of a company are driven by their brand even more than their customers.
As I see it, the AV vendor space is breaking apart into four chunks:
- Traditional AV – Focused on being lightweight and supplementing the protections built into an operating system.
- Anti-Malware – Focused on monitoring and responding to bad and potentially bad things that can happen to an operating system.
- Application Whitelisting – Focused on locking down an operating system to only allow known applications to run.
- Malware Analytics – Focused on providing detailed data about events so human analysts can make appropriate decisions.
We are also seeing the attack space splintering as well. Specifically, we’re seeing a tiered structure emerging:
- Background Radiation – A constant stream of trivial attacks, legacy viruses and worms that float about the internet.
- Industry-focused Asset Attack – Attacks that focus on specific industries aiming to steal monetary assets. These often rotate between industries, “campaign” style. At present, Western banks are in vogue. Indications are that these attacks are run by organized criminal groups. If you have above average protection in this space, you gain significant competitive advantage as attacks are driven to those that do not.
- State-sponsored IP Attack – Attacks that also focus on specific industries, but are run by better-organized groups suspected of being funded by state agencies. They aim to steal intellectual property. You get significant benefit from being above-average here too.
- Industrial Espionage – Attacks focus on specific companies and likely come from other specific companies. There is no benefit to be gained from being above-average in defense, as that just creates rapid escalation in an arms-race pattern of growth.
The third splintering effect is familiar to those of you who have heard my talks or read my comic book.
In the defense space, we have two primary trends emerging based on complexity. Both are valid, but they are completely incompatible with one another (at least on the large scale).
- Simplification – This trend involves firms who outsource much of their operations and infrastructure to managed SOC providers, cloud providers, SAAS providers, etc. The idea is that by focusing on their core business and finding trustworthy partners, they can become more nimble and therefore, more profitable.
- Complexification – This trend involves firms who increasingly centralize their infrastructure through virtualization, log management, analytics, etc. The idea is by taking more control, you can better analyze the business and find regions of improvement.
So after this rather long diversion, what does it mean for Sophos? Well, their core strength is offering administrators a solution to rapidly and consistently provide a reasonable level of protection that gives early indicators of attack. This means they’re a great fit for anti-malware up to and including the State-sponsored IP attack tier and work best in simpler environments or in simpler subsets of complex environments.
I do not think that they’re the best solution for highly-targeted complex companies, as they are not an analytics tool. They’re also not the best solution for extremely simple firms that want “set it and forget it” technologies. Security takes work and if you put the work in, you get better security. You should pick a solution that allows you to put in more work than you currently do, but does not require that additional work for the product to still be effective.
Many of the critiques of Sophos tend to be at the edges. And Sophos doesn’t help these concerns by marketing as if they fit everywhere for everyone. I think they’ll eventually reach this goal, but they’re not there today.
If you’re in a highly complex environment that is facing constant incursion from well-funded foreign governments, Sophos better not be your only tool. You need Analytics, too.
If you want the cheapest solution out there that you can install and ignore, Sophos won’t work well for you either. That’s where Traditional AV and the ability to wipe and reload when it fails comes in.
Operationally, you need to figure out what sort of attack and defense space you’re in, so you can select the tool(s) that will provide the best protection for your business. If you overlap spaces, you’re going to need multiple tools. One of the biggest reasons I really like Sophos is because of their flexibility to play in overlapping spaces. They layer quite well with other security products, which is a great benefit for their customers.
Just remember: We live in a complex world. There are no magic bullets. Security requires thought.
This article was original posted on RJS Smart Security.
Controlling the Security Story
- At November 16, 2012
- By Josh More
- In Business Security
 0
0
This is a hard article to read. For those that don’t want to read hate speech, I will briefly summarize.
On Tuesday, November 6th, the United States of America held a vote, the results of which upset a few people. Many of these people chose to express their feelings online, and were documented doing so. Because many of the individuals involved took no efforts to hide their identities, some of them were traced. Then, in a move that surprises me, Jezebel’s reporters started contacting schools to find out if the schools were aware of the situation and how they were dealing with it.
In most cases, the schools cited policies of not releasing information about minors… which I can’t fault. However, the hidden gem was Dr. Rick Brooks of Jackson Christian School, who said:
Addison’s words clearly do not reflect the values that we espouse and teach at Jackson Christian School, and are not representative of our broader school community. As such, we have visited with him about his actions and his attitude, and have disciplined him accordingly. As is our school policy, we will not share information about specific discipline cases.
Though we find Addison’s action and words deplorable, we hope that our continued encouragement and teaching will help him further avoid the mistakes of youth, and will help him to mature as a young man. I hope that you will be able to look beyond what he has done, and toward the man that he can and will become from this unfortunate learning experience.
And that, I think, is worth discussion.
People make mistakes. People grow and change. As adults, one of our social tasks is to help the young turn into people we can later respect. As employers and employees, we like to think we’re here to make money, but if that were the case, the world would be nothing but multi-level marketing. No, we need more. For many of us, we need to help others and tell stories. We love stories. In fact, the more business owners I work with, the more I find who are in business to help others … be it their customers or the employees.
Hate speech is one form of story-telling. Reporting is another.
But wait, isn’t this a security blog?
If we want to make money, we have to tell a story that’s good enough to get people to let us help them. If what we care about is helping others, we have to know when they need to be helped. If what we care about is stories, we have to know which stories are being told. Fundamentally, we have to know what’s going on.
It seems reasonable that most of these schools learned about what their students were saying after the first article was published. Basically, they learned the story that others were telling about them. They did not get to influence the narrative and were stuck in a reactive mode. Some did better than others, but if they had been listening to what others were saying, odds are the speech would have been addressed before the election.
And that is where DLP comes in. It’s marketed as Data Loss Prevention, but that’s not what it is. DLP is a story tool. It helps you identify what sorts of information exists on your network and lets you know when it leaves. It’s traditionally used for boring stuff like keeping social security and credit card numbers off the internet (sarcasm). However, like most security technologies, it can be used creatively. In this case, monitoring for a few keywords would have let the schools know quickly what students were saying (at least from the school networks). When running in non-blocking mode, it can collect data, so you can easily identify people that need improvement.
Similar internet-facing technologies can scan specific websites on a periodic basis to report the stories being told about you. This can help you identify the narratives and take corrective action for People, Processes and Technology before the story spins out of control and you’re stuck with no option but reaction.
Security technology is all too often viewed as “blocking” or prescriptive. When used properly, security technology enables the business. It helps you learn more and learn faster. This gives you control of your business, so you don’t have to keep finding your way in a world of constant attacks and errors.
(This post was originally published at RJS Smart Security)
Video – OWASP – July 16th, 2012
- At November 12, 2012
- By Josh More
- In Business Security, Psychology
 0
0
This summer, I gave a talk at the local OWASP group. Last week, I finally had time to learn OpenShot (not as hard as I thought it’d be) and today, there are two shiny new videos on YouTube.
There always seems to be a tradeoff between audio quality and video quality and I think I managed to hit the middle on this one. As I practice with techniques, I hope to make better ones. However, if I wait for perfection, I’d never post a thing, so here you go:
Here is the actual talk:
Here is the Q&A after: